Authentication
Consultation¶
Keycloak integration¶
Punch kibana plugin¶
Punch has integrated keycloack to secure advanced functions provided by the punch kibana plugin.
Keycloak description:
Keycloak is an open source software designed to allow single sign-on with Identity Management and Access Management aimed at modern applications and services.
Demo / Standalone: A short video demonstration on standalone is available on our youtube channel:
Architecture¶
Keycloak is based on a SSO architecture. A proxy is responsible to check the authentication status of a user (using a token). If a user is not authenticated, the proxy redirects the user to keycloak interface.
The keycloak has an administration interface to manage groups, roles and users.
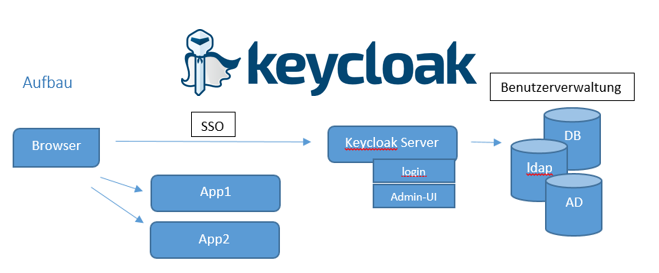
list of TCP ports:
- Keycloak Gateway (proxy): TCP/3000
- Keycloak Administration : TCP/8180
Punch plugin role¶
For the kibana plugin, punch provides the following roles:
-
pp_plugin_view: User can use Punchplatform Plugin and read the documentation -
pp_data_extraction: User can extract data from data extraction feature -
pp_configuration_view: User can read the platform configuration -
pp_configuration_edit: User can edit platform configuration (requires pp_configuration_view) -
pp_platform_channel_control: User can start/stop/reload channels (requires pp_configuration_view) -
pp_pml_view: User can view existing PML and create without save -
pp_pml_edit: User can create, delete and save PML (requires pp_pml_view) -
pp_pml_execute: User can execute PML (requires pp_pml_view) -
pp_testers_view: User can use Punch and Grok tester -
pp_ioc_view: User can use IoC lists -
pp_ioc_edit: User can create/delete IoC lists (requires pp_ioc_view)
Standalone example¶
Punch provides a standalone with a keycloak preconfigured. The keycloak client related to the punch kibana plugin of the standalone is called standalone-proxy
Here is the procedure to install and run keycloak on the standalone.
Collection¶
Certificate authentication¶
Punch platform has by design a perimetric security with the 3-Tiers network architecture. However the platform interfaces (input & output) are vulnerable.
Punch has secured the most used components:
- Syslog Spout & Bolts
- Lumberjack Spout & Bolts
These components accept an authentication with a certificate to avoid "man in the middle" or wrong customer.
The full description of the components is available here: